"Sometimes password mightn't necessary for some reasons..."
******************** Special Thanks ********************
Master Phrakrusirinantawit
***************************************************
SECTION 1 Understand Linux Security

Above is User Account. Each field is delimited by :
Types of Accounts
By default, Linux distinguishes between several account types in order to isolate processes and workloads. Linux has four types of accounts:
- root
- System
- Normal
- Network
Linux supported multi-users so these are mine. Keep in mind the rest might be Anonymous...
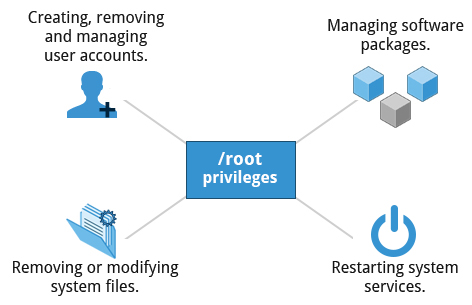
SECTION 2 User Privileges
- Regular account users of Linux distributions may be allowed to install software packages, update some settings, and apply various kinds of changes to the system. However
root originates everything. Let's imagine from bottom-up. It seems like CA root what would happen if we cut some parts of it?
How to remember:
useradd ~= just username
adduser ~= all details
Operations That Do Not Require root Privileges
A regular account user can perform some operations requiring special permissions; however, the system configuration must allow such abilities to be exercised.
SUID (Set owner User ID upon execution—similar to the Windows "run as" feature) is a special kind of file permission given to a file. SUID provides temporary permissions to a user to run a program with the permissions of the file owner (which may be root) instead of the permissions held by the user.
The table provides examples of operations which do not require root privileges:
| Operations that do not require Root privilege | Examples of this operation |
| Running a network client | Sharing a file over the network |
| Using devices such as printers | Printing over the network |
| Operations on files that the user has proper permissions to access | Accessing files that you have access to or sharing data over the network |
| Running SUID-root applications | Executing programs such as passwd. |
SECTION 3 sudo and su
who where = (as_whom) what
savant ALL = (ALL:ALL) ALL
-rw-r--r-- 1 kevin savant 57 Dec 3 22:44 paper.txt
drwxr-xr-x 5 kevin kevin 4.0K Dec 4 22:44 Downloads
This one I'm not sure...
sudo Features

sudo has the ability to keep track of unsuccessful attempts at gaining root access. Users' authorization for using sudo is based on configuration information stored in the /etc/sudoers file and in the /etc/sudoers.d directory.
A message such as the following would appear in a system log file (usually /var/log/secure) when trying to execute sudo bash without successfully authenticating the user:
authentication failure; logname=op uid=0 euid=0 tty=/dev/pts/6 ruser=op rhost= user=op conversation failed auth could not identify password for [op] op : 1 incorrect password attempt ; TTY=pts/6 ; PWD=/var/log ; USER=root ; COMMAND=/bin/bash
This sample just selects pts/0 checking by who command but actually there are others...
Process Isolation
 Linux is considered to be more secure than many other operating systems because processes are naturally isolated from each other. My point of view, it looks like multi-threads or multi-processes since they are the same binaries but located different memory blocks. One process normally cannot access the resources of another process, even when that process is running with the same user privileges. Linux thus makes it difficult (though certainly not impossible) for viruses and security exploits to access and attack random resources on a system.
Linux is considered to be more secure than many other operating systems because processes are naturally isolated from each other. My point of view, it looks like multi-threads or multi-processes since they are the same binaries but located different memory blocks. One process normally cannot access the resources of another process, even when that process is running with the same user privileges. Linux thus makes it difficult (though certainly not impossible) for viruses and security exploits to access and attack random resources on a system.
Additional security mechanisms that have been recently introduced in order to make risks even smaller are:
- Control Groups (cgroups): Allows system administrators to group processes and associate finite resources to each cgroup.
- Linux Containers (LXC): Makes it possible to run multiple isolated Linux systems (containers) on a single system by relying on cgroups.
- Virtualization: Hardware is emulated in such a way that not only processes can be isolated, but entire systems are run simultaneously as isolated and insulated guests (virtual machines) on one physical host.
Hardware Device Access
Linux limits user access to non-networking hardware devices in a manner that is extremely similar to regular file access. Applications interact by engaging the filesystem layer (which is independent of the actual device or hardware the file resides on). This layer will then opens a device special file (often called a device node) under the /dev directory that corresponds to the device being accessed. Each device special file has standard owner, group and world permission fields. Security is naturally enforced just as it is when standard files are accessed.
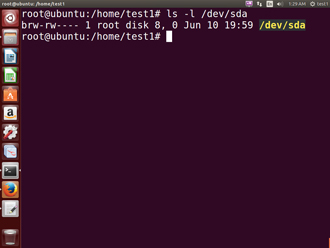
Hard disks, for example, are represented as /dev/sd*. While a root user can read and write to the disk in a raw fashion. For example, by doing something like:
$ echo hello world > /dev/sda1
the standard permissions as shown in the figure make it impossible for regular users to do so. Writing to a device in this fashion can easily obliterate the filesystem stored on it in a way that cannot be repaired without great effort, if at all. The normal reading and writing of files on the hard disk by applications is done at a higher level through the filesystem, and never through direct access to the device node.
Keeping Current
When security problems in either the Linux kernel or applications and libraries are discovered, Linux distributions have a good record of reacting quickly and pushing out fixes to all systems by updating their software repositories and sending notifications to update immediately. The same thing is true with bug fixes and performance improvements that are not security related.
However, it is well known that many systems do not get updated frequently enough and problems which have already been cured are allowed to remain on computers for a long time; this is particularly true with proprietary operating systems where users are either uninformed or distrustful of the vendor's patching policy as sometimes updates can cause new problems and break existing operations. Many of the most successful attack vectors come from exploiting security holes for which fixes are already known but not universally deployed. It seems like to inform those who pay you to take risk...
So the best practice is to take advantage of your Linux distribution's mechanism for automatic updates and never postpone them. It is extremely rare that such an update will cause new problems.
SECTION 4 PASSWORDS
Password Encryption
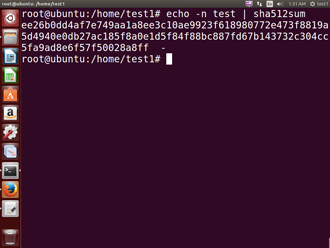
Protecting passwords has become a crucial element of security. Most Linux distributions rely on a modern password encryption algorithm called SHA-512 (Secure Hashing Algorithm 512 bits), developed by the U.S. National Security Agency (NSA) to encrypt passwords.
The SHA-512 algorithm is widely used for security applications and protocols. These security applications and protocols include TLS, SSL, PHP, SSH, S/MIME and IPSec. SHA-512 is one of the most tested hashing algorithms.
For example, if you wish to experiment with SHA-512 encoding, the word “test” can be encoded using the program sha512sum to produce the SHA-512 form (see graphic):
Recheck with website SHA512 got the same HASH
Good Password Practices
IT professionals follow several good practices for securing the data and the password of every user.
- Password aging is a method to ensure that users get prompts that remind them to create a new password after a specific period. This can ensure that passwords, if cracked, will only be usable for a limited amount of time. This feature is implemented using chage, which configures the password expiry information for a user.
- Another method is to force users to set strong passwords using Pluggable Authentication Modules (PAM). PAM can be configured to automatically verify that a password created or modified using the passwd utility is sufficiently strong. PAM configuration is implemented using a library called pam_cracklib.so, which can also be replaced by pam_passwdqc.so for more options.
- One can also install password cracking programs, such as John The Ripper, to secure the password file and detect weak password entries. It is recommended that written authorization be obtained before installing such tools on any system that you do not own.
SECTION 5 BOOT LOADER PASSWORDS
GRUB 2 should display a version number of 1.96 or later. Legacy GRUB is version 0.97.
Hardware Vulnerability
When hardware is physically accessible, security can be compromised by:
- Key logging: Recording the real time activity of a computer user including the keys they press. The captured data can either be stored locally or transmitted to remote machines
- Network sniffing: Capturing and viewing the network packet level data on your network
- Booting with a live or rescue disk
- Remounting and modifying disk content
Your IT security policy should start with requirements on how to properly secure physical access to servers and workstations. Physical access to a system makes it possible for attackers to easily leverage several attack vectors, in a way that makes all operating system level recommendations irrelevant.
The guidelines of security are:
- Lock down workstations and servers
- Protect your network links such that it cannot be accessed by people you do not trust
- Protect your keyboards where passwords are entered to ensure the keyboards cannot be tampered with
- Ensure a password protects the BIOS in such a way that the system cannot be booted with a live or rescue DVD or USB key
For single user computers and those in a home environment some of the above features (like preventing booting from removable media) can be excessive, and you can avoid implementing them. However, if sensitive information is on your system that requires careful protection, either it shouldn't be there or it should be better protected by following the above guidelines.
↞ Summary ↠

- The root account has authority over the entire system.
- root privileges may be required for tasks, such as restarting services, manually installing packages and managing parts of the filesystem that are outside your home directory.
- In order to perform any privileged operations such as system-wide changes, you need to use either su or sudo.
- Calls to sudo trigger a lookup in the /etc/sudoers file, or in the /etc/sudoers.d directory which first validates that the calling user is allowed to use sudo and that it is being used within permitted scope
- One of the most powerful features of sudo is its ability to log unsuccessful attempts at gaining root access. By default sudo commands and failures are logged in /var/log/auth.log under the Debian family and /var/log/messages in other distribution families.
- One process cannot access another process’ resources, even when that process is running with the same user privileges.
- Using the user credentials, the system verifies the authenticity and identity.
- The SHA-512 algorithm is typically used to encode passwords. They can be encrypted but not decrypted.
- Pluggable Authentication Modules (PAM) can be configured to automatically verify that passwords created or modified using the passwd utility are strong enough (what is considered strong enough can also be configured).
- Your IT security policy should start with requirements on how to properly secure physical access to servers and workstations.
- Keeping your systems updated is an important step in avoiding security attacks.
References: